Authenticating SSL VPN users using LDAP
- Registering the LDAP server on the FortiGate
- Importing LDAP users
- Creating the SSL VPN user group
- Creating the SSL address range
- Configuring the SSL VPN tunnel
- Creating security policies
Registering the LDAP server on the FortiGate
· Go to User & Device > Authentication > LDAP Servers and select Create New.
· Enter the LDAP Server’s FQDN or IP in Server Name/IP. If necessary, change the Server Port Number (the default is 389.)
· Enter the Common Name Identifier. Most LDAP servers use “cn” by default.
· In the Distinguished Name field, enter the base distinguished name for the server, using the correct X.500 or LDAP format.
· Set the Bind Type to Regular, and enter the LDAP administrator’s distinguished name and password for User DN and Password.
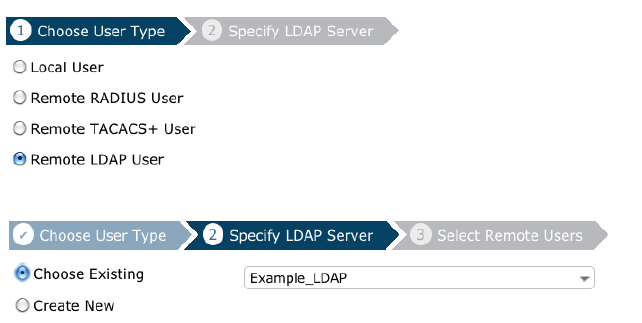
Importing LDAP users
· Go to User & Device > User > User Definition, and create a new user, selecting Remote LDAP User.
· Choose your LDAP Server from the dropdown list. You will be presented with a list of user accounts, filtered by the LDAP Filter to include only common user classes.
Note:
· With a properly configured LDAP server, user and authentication data can be maintained independently of the FortiGate, accessed only when a remote user attempts to connect through the SSL VPN tunnel.
· Instead of using fetching user always recommended to create VPN group on AD and map with fortigate Group.